Activities associated with Koobface have increased during the month of December. Often it is for the sending of traffic to compromised servers in order to obtain more servers. Other times the activity centers around using those same compromised servers to proxy users to malicious domains that are then used for further distribution of malware or command and control of the infected machines.
I noticed a trend with some of the domain-based locations making use of the holiday theme. This has included everything from “presents for your pets” to “festive holiday trees” – these are domains that appear legitimate but are not. In fact, many of the domains that are being used were legitimate at one point and now are serving a different, more questionable purpose.
The messages Look like:
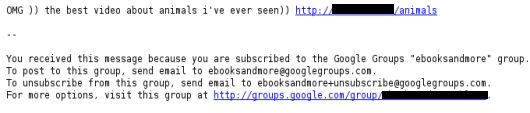
and When you follow link:
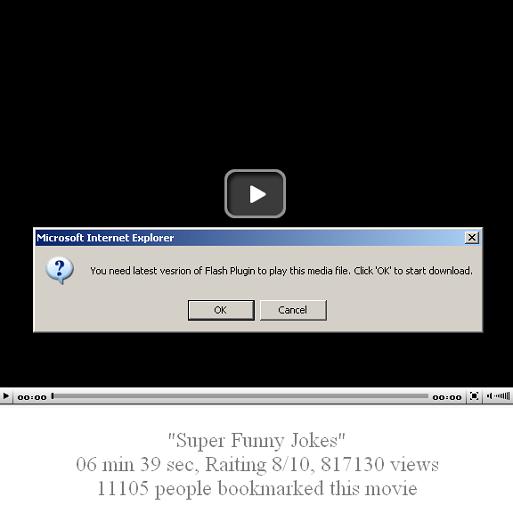
By Clicking OK…:
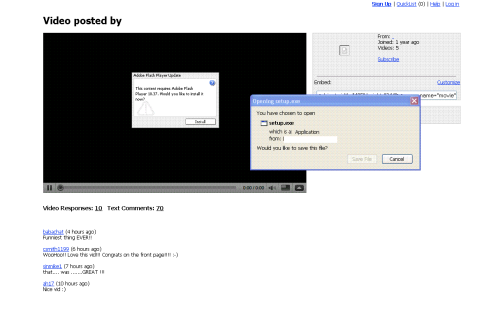
starting to sound familiar?
It also insists the plugin be installed by means of never ending popup windows.
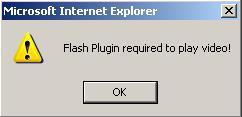
This is a typical case of malware posing as plugins required for playing videos.
The advice here is to avoid following links contained in these kind of emails. Not enabling javascript will also help in this case, and if stuck in endless popup loop there is always the last option of killing the browser process (through task manager or other means).
When users go to these sites for these happy holiday thoughts – they are instead instantly greeted by having files downloaded to their computers. And voila – a lovely “gift” is attempting to execute upon them. The gift of holiday identity theft!
I have been monitoring the progress of this attack as it rides upon the Holiday Cheer and its spread continued throughout the day – and based upon past trends – I expect it to continue to evolve and find new servers and methods with similar associations over the next few weeks.
Stay updated and safe over the holidays!