Malware authors love to innovate when it comes to persistence and hiding their nefarious creations from detection, and although most of the schemes are not unknown to analysts, they still show that malware authors are constantly on the prowl and evolving their techniques.
The example I have is of yet another registry-centric malware which by the nature of its construction has several advantages to defeating naive security software. The sample, detected as Troj/RegExec-A, is essentially a multi-component threat of sorts comprising of at least 3 components (Dropper/installer, Payload and Loader.)
The dropper or installer component sets up the registry key and possibly some default payload and then installs the Loader component to be auto-launched by any number of autorun methods. By splitting functionality into several components the malware authors are hoping that when the initial component is detected, the active components go un-noticed, but more importantly, hiding that which draws most suspicion in the place least likely to be scanned.
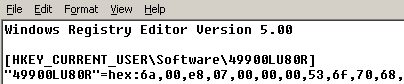
Jamming malcode into the registry also has the advantage of being easily updatable by a textual .reg file which the victim need only to double-click on…
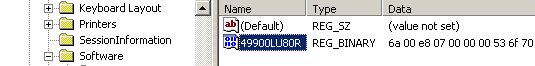
The loader component is hooked into the AppInit_DLLs key and thus loaded by user32.dll (effectively linking it to most system components) but to the untrained eye this loader component appears to just read a registry key.
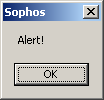
In reality, the loader allocates some memory, reads the contents of its registry entry into said buffer and then passes control to it (in my example this results in a MessageBox however this could be any arbitrary code.)
Due to the ingenuity and persistence of the malware authors it is thus important to manage and maintain your security software, both at the gateway as well as the endpoint, but these are still no substitute for good web-surfing practice.