According to latest State of Spam and Phishing report, scam and phishing messages accounted for 21 percent of all spam, which is the highest level recorded since the inception of the report. For comparison, these types of spam represented only 10 percent of total spam a year ago.
Historically, the primary vector for spam attacks was to blast out as many messages as possible, hoping that someone would open a message and click on the call to action. The call to action could be anything from clicking on a link to purchase medications, to visiting an adult website. While we continue to see high volumes of spam originating from expansive botnets, spammers are also moving towards a sophisticated and more targeted approach to spam. Two primary examples of this trend are 419/Nigerian type scams and phishing messages.
While 419 spam (a.k.a., the Nigerian scam) has been around for a long time, the content that the spammer uses to trick the email recipient has evolved over time. In the early days, spammers used the “next of kin” approach: a message would inform the user that some wealthy person died with no next of kin, and someone (the user) must file a claim to gain access to the massive inheritance. Spammers also used the “international lotto” technique: a message would inform the user that s/he has been selected as a winner of an international lottery.
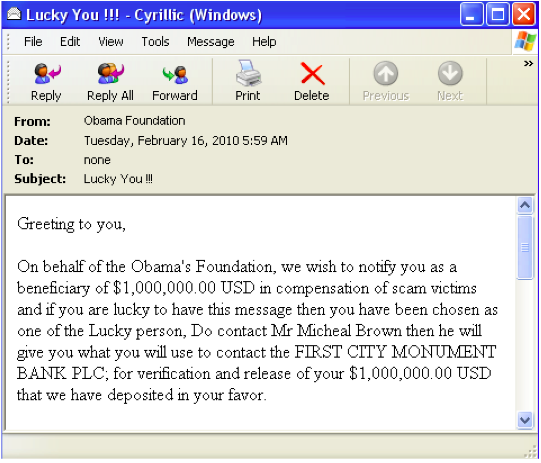
In an effort to make such 419 spam more credible, spammers have started using various current events and other types of social engineering to trick email recipients. As we highlighted previously, spammers have used the tragic Haitian and Chile earthquakes as bylines to ask users to donate money. Any donation, of course, would go to these scammers and not to those in legitimate need. These attacks can also compromise credit card or bank information for broader financial exposure. In another example below, spammers used President Obama’s name to get users’ attention:
Phishing messages are even more dangerous than 419 scams. While users lose money when they fall victim to 419 scams, they can lose even more if they fall victim to a phishing message: their identities. These phishing messages have also grown to be more sophisticated and targeted over time.
In the early days, phishing attacks generally used the names of large financial institutions with a nationwide footprint. The spammers hoped that the email recipient would have an account with the financial institution being used as a phishing lure. We also saw attempts to use online services with a large user base, again hoping that the recipient had an account with that service provider.
In recent attacks, however, we are seeing more targeted phishing attempts. For example, rather than using a large financial institution, spammers are using a small local credit union and are only sending messages to users in the area that the credit union serves. This makes the phishing message more credible to end users because there is a better chance of them having an account with that bank.
Spammers are also evolving beyond the financial institutions typically used in a phishing message. They used the Haiti earthquake to their advantage and asked for personal information while pretending to be UNICEF.
We have also seen other phishing attempts where the spammers used other lures such as adult pornography, as mentioned in the blog post Phishing Using Pornographic Content as Bait.
As the spammers continue to innovate with new 419 and phishing techniques, email users must stay vigilant and not fall victim to their tricks. For a general guideline on protecting yourself from these attacks, please refer to the “Checklist: Protecting your business, your employees and your customers” section in my site.