Hi folks,
One of our researchers recently discovered that the Liberty exploit kit included a fairly new exploit from November 2009 … http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2009-3867 .
The fact that there was something fairly new in terms of exploits was interesting to start with, but then we looked at the text on the exploit page….
Lehman Brothers?! Coffee Party??!! Holy Activists, Batman!!! It’s politically motivated!!!!
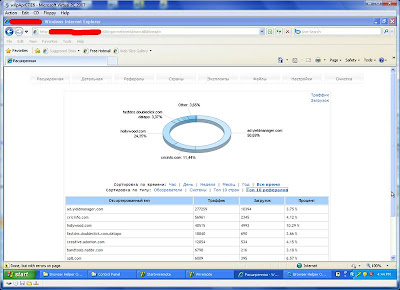
Then we looked at the stats page (all these toolkits come with a sophisticated admin page), and saw that the top referrer was ad.yieldmanager.com! Holy Advertisers, Batman! Activists who know how to use exploit kits, _and_ the ad network!!!
Then we looked at another commonly reported Liberty Exploit kit site, and saw the text about Coffee Party replaced by talk about unrelated stories about storms and Toyotas …
First mystery solved… it was not an exploit-loving activist… it’s just a place where the evil webmaster puts some newsie text, probably to prevent the page being empty and looking suspicious.
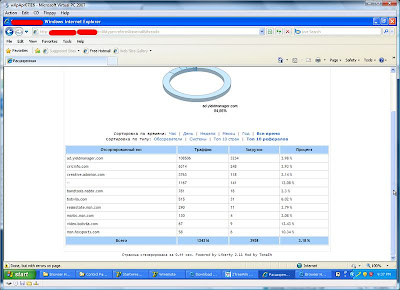
Next we looked at the stats page for this site, and found some really interesting referrers….
Now I’m not saying that Liberty is being served up by ad networks, but the stats pages for the exploit kits are certainly saying that. And if their stats are to be believed, it’s interesting how even visiting major websites can allow you to be drawn to an attack site. It really underscores the futility of blacklisting websites. It’s mostly pointless. Best idea is real-time analysis of webpages, just as LinkScanner does.
It’s a tricky world out there folks… keep safe.
 Omid Farhang
Omid Farhang