When it is not actually a picture but an obfuscated malicious VB script!
That’s the story with W32/VBSAuto-F — yet another autorun worm that sets a number of self-starting registry entries, spreads via USB drives, and downloads further malware. The worm embeds code in a JPEG comment field of an ambiguously named file “image.jpg” or “imwin.jpg”.
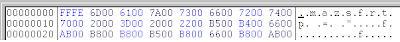
Previewing such files as images remains innocuous, as picture viewers tend not to execute meta data by default. This is unfortunately not the case when the file is run through the VB script engine, which is happy to interpret the same JPEG comment 0xFFFE header bytes to indicate Little-Endian UTF-16 encoded data and execute the remaining portion of the file as code.
This malware is certainly not worth 1000 words, as even the deobfuscated malicious script itself weighs in at a mere 391 words total. Though for Sophos customers, there is one word that applies appropriately — protected.
 Omid Farhang
Omid Farhang