Microsoft researchers found a cross-platform botnet that originates from malicious software downloads on Windows devices & succeeds in propagating to a variety of Linux-based devices by enumerating default credentials on internet-exposed SSH-enabled devices.
Microsoft researchers observed that the initial infection points related to the botnet were devices infected through the installation of malicious cracking tools that purport to acquire illegal Windows licenses. The cracking tools contain additional code that downloads and launches a fake version of svchost.exe through a PowerShell command. In some cases, the downloaded file is named svchosts.exe.
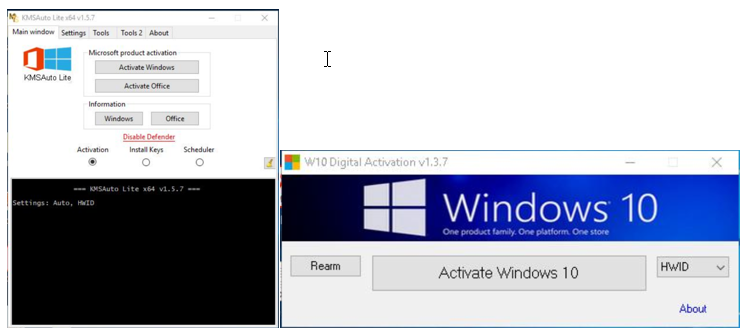
Cracking tools used to spread the botnet. rmicrosoft.com
Continue Reading at Microsoft Security Blog
Thanks to @VirusBulletin for sharing.