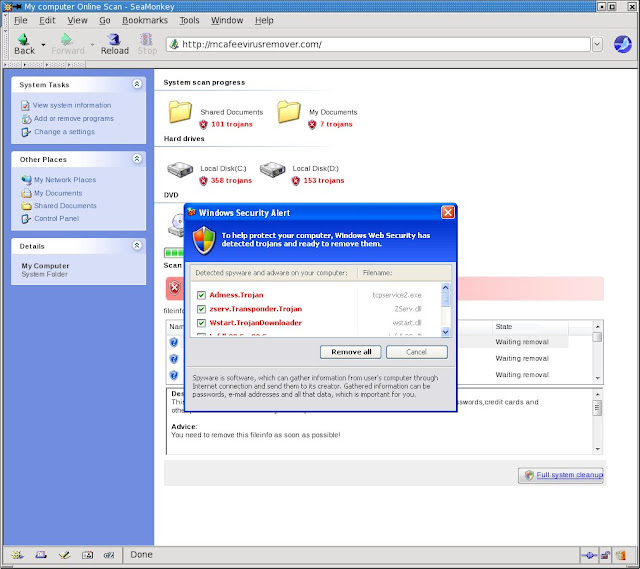
Cybercriminals love to use social engineering techniques to trick users into installing their malware. One of the latest fake-alert variants attempts to trick users into believing the software is related to or hosted by McAfee:mcafeevirusremover.com.
The script hosted by the domain can attack the Windows browsers Internet Explorer, Mozilla Seamonkey, and Chrome. The script also affects browsers on Linux platforms.
This fake-alert variant is hosted on at least 13 other known domains. McAfee’s Trusted Source blocks the IP addresses and the domains (including DNS and mail servers) associated with this Trojan. For example:
The infection begins by redirecting the victim to the domain hosting the Trojan script code. This website is designed to look like Windows Explorer in Windows XP. It “reports” multiple infections on the victim’s computer:
If the user clicks anything within the browser, the SecurityTool Malware will download.
 Omid Farhang
Omid Farhang