Koobface is still going strong despite not making the headlines so much anymore. Well, the Koobface gang took the time to send a Christmas card and wish security researchers a happy new year. Very nice of them…
For a couple of days now I’ve been looking at their infection method and trying to see any interesting patterns.
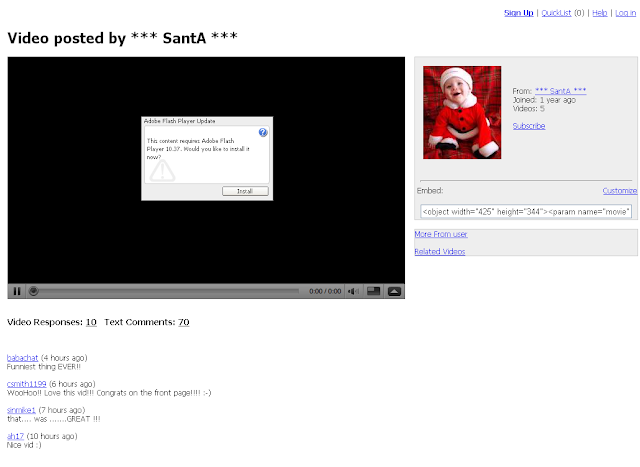
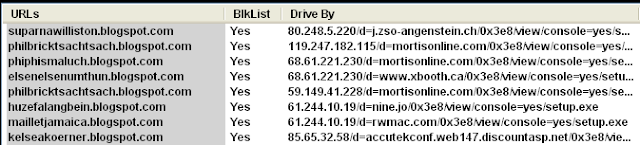
The bad guys use bogus blogpost.com blog pages to redirect users to the actual Koobface malware. The redirection consists of several attempts to connect to compromised PCs, through their IP address. Below is a Fiddler log showing those attempted connections (in red are failed connections). Once a host has successfully responded, the users are redirected to a fake page prompting them to install a video codec.
Typical social engineering used to lure the user into installing the malware:
The common traits for the Koobface infection process are:
– a malicious / redirect blogspot.com page
– an infected PC hosting the malware
If you look in more detail at the blogspot.com pages, they reveal some interesting things too:
The pages use SEO and social engineering tricks to be ranked high in Google searches. Basically, anything that makes the headlines in the real world is going to generate interest and therefore traffic. That’s exactly what the Koobface gang is after!
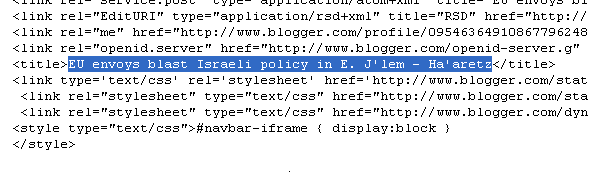
Now not all malicious blogspot.com pages use the same titles… But, if you can indentify a new title you can harvest many more malicious pages.
Here is an example: I found yet another string of keywords used by the Koobface gang in one of their blogspot.com pages. (Download the page locally with wget and then take a look at the source code).
Then do a Google search following that structure:
site:blogspot.com intitle:”XXXXXXXXXXXXXXXXX”
where XXXXXXXXXXXXXXXXX is the catch phrase used by the Koobface criminals.
What you get are similar pages that will redirect you to more infected PCs:
 Omid Farhang
Omid Farhang